|
21.03.2022 22:57:00
|
Cybersecurity Posture Improved With Identity Security Architecture, Says Info-Tech Research Group
TORONTO, March 21, 2022 /PRNewswire/ - Global IT research and advisory firm Info-Tech Research Group has released a new research blueprint to help security leaders build an identity security architecture. The blueprint will allow them to understand and mitigate their organization's cybersecurity weaknesses.
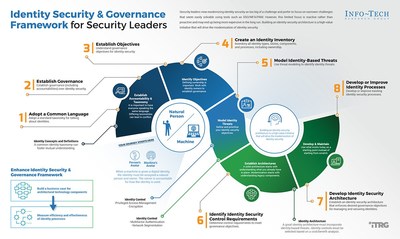
Info-Tech Research Group has developed an effective approach for security leaders to build an identity security architecture. This new research blueprint includes tools for establishing governance for identity security, creating an identity inventory, modeling identity-based threats, and building an identity security architecture.
In 2020, the world saw a mass digital migration. However, the migration did not come with a secure transition. The move to remote work has significantly contributed to increases in stolen data. For the third year in a row, identity security has been one of the weakest links in any security program. Weak identity controls, which is a problem for many organizations, have continually given bad actors an easy path to gaining access to enterprise data.
"To ensure a significant improvement in identity security, organizations must be willing to take a step back and understand where the vulnerabilities lie and identify the threats that may take advantage of them," says Research Director Ian Mulholland. "Every organization likely juggles many different identity types. This results in a complex system of identity storage, ownership, and security requirements."
Security leaders view modernizing identity security as too big of a challenge. They instead prefer to focus on narrower challenges that seem more easily solvable using such tools as single sign-on, multifactor authentication, or privileged access management. However, this limited focus is reactive rather than proactive, and it may end up being more expensive in the long run.
"The first step to improving anything related to identity security will be to fully understand all the different identities that exist, where they exist, who owns related processes, and what threats exist that might take advantage of a managed identity," explains Mulholland. "Only when an organization has successfully catalogued the information necessary to secure all their identities can they build an identity security architecture that describes an approach to identity security befitting the modern era."
For most organizations, identity and access management has been allowed to grow organically, and it has become inflexible and difficult to control. In most cases, the number of identities and the items they access has increased with each passing year, necessitating more scalable processes and technology. Info-Tech suggests the following identity security and governance framework and strategy for security leaders:
Over time, organizations will experience incremental value from knowing the vectors through which they can be attacked. Through continual updates, security protocols will evolve with less associated effort, time, and costs.
Info-Tech maintains that strong identity security and governance are the keys to the zero trust future.
To learn more about Info-Tech Research Group and to download our latest research, visit www.infotech.com and connect via LinkedIn, Twitter, and Facebook.
Media professionals are encouraged to register for Info-Tech's Media Insiders program for more research and insights. This program provides unrestricted, on-demand access to IT, HR, and software industry content and subject matter experts from a group of more than 200 research analysts. To apply for access, contact pr@infotech.com.
Supporting Resources
- Download the complete Assess and Govern Identity Security blueprint.
About Info-Tech Research Group
Info-Tech Research Group is the world's fastest-growing information technology research and advisory firm, proudly serving over 30,000 IT professionals. The company produces unbiased and highly relevant research to help CIOs and IT leaders make strategic, timely, and well-informed decisions. Info-Tech partners closely with IT teams to provide them with everything they need, from actionable tools to analyst guidance, ensuring they deliver measurable results for their organizations.
![]() View original content to download multimedia:https://www.prnewswire.com/news-releases/cybersecurity-posture-improved-with-identity-security-architecture-says-info-tech-research-group-301507132.html
View original content to download multimedia:https://www.prnewswire.com/news-releases/cybersecurity-posture-improved-with-identity-security-architecture-says-info-tech-research-group-301507132.html
SOURCE Info-Tech Research Group
 Der finanzen.at Ratgeber für Aktien!
Der finanzen.at Ratgeber für Aktien!
Wenn Sie mehr über das Thema Aktien erfahren wollen, finden Sie in unserem Ratgeber viele interessante Artikel dazu!
Jetzt informieren!