|
15.12.2023 21:06:00
|
A New Era in Cybersecurity: Info-Tech Research Group's Roadmap for Automating and Strengthening Security Operations
Info-Tech's latest blueprint emphasizes the critical role of a strategic cybersecurity automation roadmap, which can significantly enhance an organization's defense mechanisms, responsiveness, and efficiency in the face of evolving cyberthreats in today's complex digital environment.
TORONTO, Dec. 15, 2023 /PRNewswire/ - As cybersecurity threats become increasingly sophisticated and automated, the need for robust security processes has never been more pressing. With security teams now grappling with the challenges of alert overload, siloed tools, and manual processes, the adoption of automation in security operations is emerging as a key solution. However, implementing automation poses its own set of challenges, from steep learning curves to justifying costs and overcoming organizational resistance. To guide organizations through these complexities and maximize the benefits of automation, global IT research and advisory firm Info-Tech Research Group has released its latest research-backed blueprint, Build an Automation Roadmap to Streamline Security Processes.
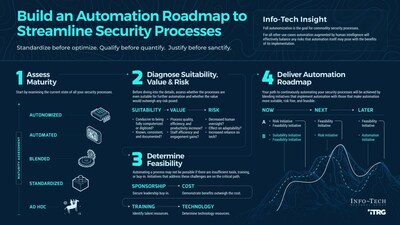
The firm's essential resource provides in-depth insights and practical tools to help organizations navigate the intricacies of security process automation, laying out a clear path for assessing the maturity of current security processes, identifying key areas for automation, and developing a comprehensive roadmap.
"Information security practitioners are burnt out as the majority of their time is spent on tedious manual work," says Fred Chagnon, principal research director at Info-Tech Research Group. "That manual work, which probably has to be done to meet compliance regulations, isn't being done with the speed and accuracy needed for effective protection and defense – not when we know the attackers themselves are increasingly making use of advanced automation tools powered by AI. The engineers and operations staff know this, and it only fuels their disengagement."
Info-Tech's research delves into the substantial benefits of automating security processes, marking a departure from traditional labor-intensive security practices to more efficient automated systems. The firm's analysis highlights how automation can transform the security landscape, enabling teams to manage tasks with greater speed and precision. This shift is crucial for keeping pace with rapidly evolving cyberthreats. By automating routine and repetitive tasks, security professionals can focus on more strategic initiatives, enhancing their organization's overall security posture.
The adoption of a well-structured automation roadmap is quickly becoming essential for organizations aiming to bolster their defenses, reduce the risk of human error, and maintain a strong security stance in a complex digital environment.
"Implementing automation for security processes itself is hard. For example, it's a challenge to streamline processes with automation when each of the 50 technology tools that the average enterprise uses for cyber defense doesn't integrate nicely with any other," explains Chagnon. "An automation roadmap should be multifaceted. It includes initiatives that make automation more suitable for some processes, more valuable and less risky for others, and more feasible in some cases. In this way, security practitioners are automating what they can and should, as well as identifying and removing the barriers that are preventing automation from happening at all."
The firm's research further underscores that implementing automation in security processes is more than just a technological upgrade; it represents a strategic shift in how cybersecurity is approached and managed. This comprehensive framework empowers security leaders not only to streamline and automate their security operations but also to proactively identify and address potential barriers to automation.
The blueprint outlines a four-step roadmap for security leaders to automate security processes:
Info-Tech's resource underscores the transformative impact of a well-structured automation roadmap in fortifying an organization's security posture. By adopting this multifaceted approach, organizations can enhance their security posture, making it more agile, responsive, and effective against the sophisticated threats of the digital age.
The roadmap provides security leaders with a strategic process for evaluating and implementing automation, ensuring that each step taken contributes to a more robust and resilient security infrastructure. In doing so, organizations can ensure they are not merely reacting to technological advancements but proactively leveraging them to strengthen their defenses.
For exclusive media commentary from Fred Chagnon, an expert in cybersecurity and privacy, or to access the complete Build an Automation Roadmap to Streamline Security Processes research, please contact pr@infotech.com.
About Info-Tech Research GroupInfo-Tech Research Group is one of the world's leading information technology research and advisory firms, proudly serving over 30,000 IT professionals. The company produces unbiased and highly relevant research to help CIOs and IT leaders make strategic, timely, and well-informed decisions. For 25 years, Info-Tech has partnered closely with IT teams to provide them with everything they need, from actionable tools to analyst guidance, ensuring they deliver measurable results for their organizations.
Media professionals can register for unrestricted access to research across IT, HR, and software and over 200 IT and industry analysts through the firm's Media Insiders program. To gain access, contact pr@infotech.com.
For information about Info-Tech Research Group or to view the latest research, visit infotech.com and connect via LinkedIn and X.
![]() View original content to download multimedia:https://www.prnewswire.com/news-releases/a-new-era-in-cybersecurity-info-tech-research-groups-roadmap-for-automating-and-strengthening-security-operations-302017061.html
View original content to download multimedia:https://www.prnewswire.com/news-releases/a-new-era-in-cybersecurity-info-tech-research-groups-roadmap-for-automating-and-strengthening-security-operations-302017061.html
SOURCE Info-Tech Research Group
 Der finanzen.at Ratgeber für Aktien!
Der finanzen.at Ratgeber für Aktien!
Wenn Sie mehr über das Thema Aktien erfahren wollen, finden Sie in unserem Ratgeber viele interessante Artikel dazu!
Jetzt informieren!